In this article, we explore the reverse engineering errors and the corresponding fixes found in BOMB.EXE.
BOMB.EXE Overview and Purpose
BOMB. EXE is a malicious software that requires reverse engineering to identify errors and find fixes. It is essential to understand its purpose and behavior to effectively combat it. Reverse engineering BOMB.
EXE involves analyzing its code and uncovering its secrets. This process helps in identifying the malware’s network connections, browser interactions, and data exfiltration methods. By examining the software’s behavior, incident response teams can assess the risk it poses to systems and networks. Reverse engineering also helps in detecting spyware and identifying indicators of compromise.
Through this process, vendors can develop effective countermeasures and improve their malware detection engines. Reverse engineering BOMB. EXE is a crucial part of the journey to secure systems and protect against future attacks.
Is BOMB.EXE Safe? An Analysis
BOMB.EXE is a potentially harmful software that requires careful analysis. Reverse engineering errors in the BOMB.EXE binary can lead to serious security risks and vulnerabilities. It is important to take immediate action to fix these errors and ensure the safety of your system.
To start, use a reliable malware analysis service or sandbox such as Falcon Sandbox to analyze the BOMB.EXE binary. This will help identify any potential threats and provide insights on how to fix them.
During the analysis, pay attention to the network connections established by BOMB.EXE. Check if it contacts any suspicious hosts or cloud services. Additionally, look for any indicators of spyware or malicious behavior, such as unauthorized POSTs or unusual network behavior.
If you have access to the source code, conduct a thorough review to identify and fix any coding errors or vulnerabilities. This will help improve the security of the software.
Remember, a comprehensive risk assessment is crucial in determining the potential impact of BOMB.EXE on your system. Use tools like Fingerprint and Network Behavior to gather more details and understand the full scope of the threat.
Origins and Creator of BOMB.EXE
The origins of BOMB.EXE are still unknown, and the creator remains anonymous. BOMB.EXE is a malicious software that has been causing havoc for users across various platforms. It is believed to have been created using software reverse engineering techniques to exploit vulnerabilities in popular browsers like Chrome and Firefox.
The journey of BOMB.EXE begins with innocent-looking downloads from websites, SoundCloud, or even cloud services. Once executed, the BOMB.EXE binary establishes a network connection and starts wreaking havoc on the victim’s system.
To understand its behavior and identify potential fixes, experts have subjected BOMB.EXE to malware analysis services like Falcon Sandbox. Incident response teams have conducted risk assessments and performed detailed writeups to share their findings and help users protect themselves.
Despite its elusive nature, efforts are being made to uncover the secrets behind BOMB.EXE and develop solutions to mitigate its harmful effects.
BOMB.EXE Usage and Associated Software
- BOMB.EXE: The main executable file that is being reverse engineered
- Reverse engineering process for BOMB.EXE
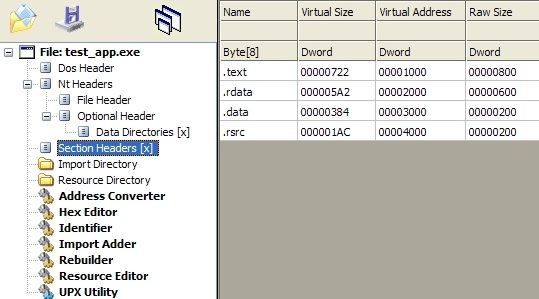
- Analysis of BOMB.EXE functionality
- Identification of errors in BOMB.EXE code
- Possible fixes for identified errors
- Associated software used in reverse engineering BOMB.EXE
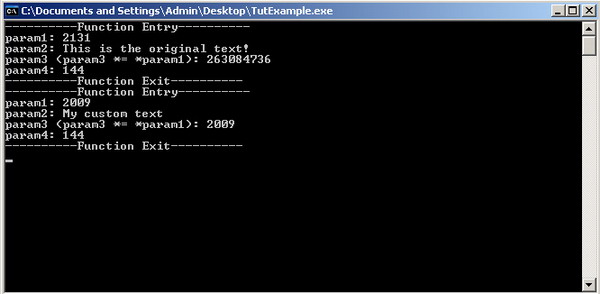
- Debugging tools for BOMB.EXE
- Disassemblers and decompilers for BOMB.EXE
- Code analysis and static analysis tools for BOMB.EXE
- Dynamic analysis tools for BOMB.EXE
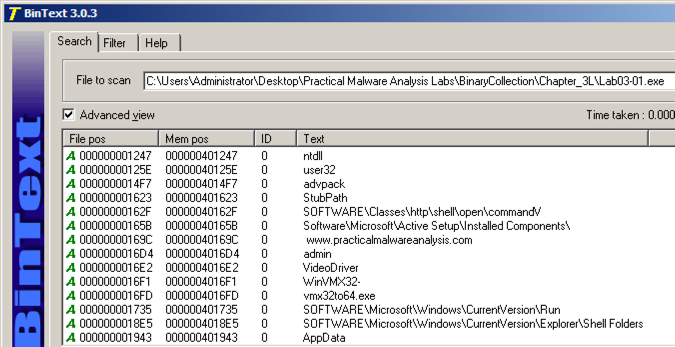
- Hex editors and binary viewers for BOMB.EXE
- Memory dump and process monitoring tools for BOMB.EXE
- Other relevant software for reverse engineering BOMB.EXE
Understanding BOMB.EXE as Malware
BOMB.EXE is a known malware that requires understanding and attention. When it comes to reverse engineering errors and fixes, there are a few key things to keep in mind.
Firstly, analyze the bomb binary to identify any vulnerabilities or malicious code. This can be done using software reverse engineering techniques or by utilizing a malware analysis service.
Next, focus on fixing the errors found during the analysis. This may involve patching the code, removing malicious components, or strengthening security measures.
It’s important to consider the risk assessment and potential impact of the malware. Determine if it has the ability to spread through network connections or exploit vulnerabilities in browsers or other software.
Lastly, keep in mind that reverse engineering BOMB.EXE is just one part of the process. It’s crucial to stay informed about the latest malware threats, regularly update security measures, and conduct ongoing monitoring and analysis.
Troubleshooting BOMB.EXE Issues
- Installation issues: Troubleshoot problems related to BOMB.EXE installation.
- Compatibility problems: Identify and resolve compatibility issues with different operating systems or hardware configurations.

- Runtime errors: Analyze and fix errors that occur during the execution of BOMB.EXE.
- Crashes and freezes: Address issues that cause BOMB.EXE to crash or freeze during operation.
- Performance optimization: Optimize BOMB.EXE to enhance its speed and efficiency.
- Memory leaks: Identify and resolve memory leaks that can cause BOMB.EXE to consume excessive system resources.

- Security vulnerabilities: Patch any security vulnerabilities that may exist in BOMB.EXE to prevent unauthorized access or attacks.
- Debugging techniques: Learn debugging strategies to identify and fix errors in BOMB.EXE.
- Updating BOMB.EXE: Keep BOMB.EXE up to date with the latest patches and bug fixes.
- Backup and recovery: Implement backup and recovery procedures to protect data and recover from potential data loss.
BOMB.EXE Running in the Background: Impact and Solutions
BOMB.EXE running in the background can have a significant impact on your system’s performance and security. If you encounter this issue, there are several solutions you can try to fix it.
First, scan your system using reliable antivirus software to detect and remove the BOMB.EXE binary. Be sure to keep your antivirus program and virus definitions up to date to ensure the best detection rate.
Next, check your browser extensions in Chrome or Firefox for any suspicious or unfamiliar ones. Remove any that you don’t recognize or trust.
If you suspect BOMB.EXE is being triggered by a specific website or webserver, clear your browser cache and cookies or try accessing the site in a private browsing window.
Update your operating system and applications to the latest version to patch any vulnerabilities that BOMB.EXE may exploit.
Consider monitoring your network connection for any unusual activity or traffic. Use a reliable network monitoring tool to detect any suspicious POSTs or unauthorized data transfers.
If you have the technical expertise, conduct a reverse engineering analysis on the BOMB.EXE binary to understand its behavior and develop effective countermeasures. This may involve examining the source code, analyzing its execution flow, and identifying any malicious functions or parts.
High CPU Usage Caused by BOMB.EXE
If you are experiencing high CPU usage caused by BOMB. EXE, there are a few fixes you can try. First, you can use a process manager to end the BOMB. EXE process. This should stop the high CPU usage immediately.
Another option is to delete the BOMB. EXE file from your system. This will permanently remove the source of the high CPU usage. If you are unsure of how to do this, you can search for a guide specific to your operating system. Additionally, you can run a malware scan on your computer using a reputable antivirus software.
This will help detect and remove any other potential threats.
BOMB.EXE as a System File: Importance and Risks
BOMB.EXE is a system file that plays a crucial role in the functioning of a computer. However, it also carries certain risks that need to be addressed.
To ensure the proper operation of BOMB.EXE, it is important to understand its structure and function. Reverse engineering can help identify errors and find fixes for them.
When reverse engineering BOMB.EXE, it is essential to consider various factors. The file may contain a binary code that can be analyzed using specialized tools. It is also helpful to refer to writeups and articles from experts in the field.
One common error that can occur with BOMB.EXE is a faulty fingerprint, which can lead to compatibility issues with certain platforms. It is necessary to test the file on different systems to ensure its compatibility.
Additionally, BOMB.EXE may have certain vulnerabilities that can be exploited by malicious actors. Regular updates and patches are crucial to address these security risks.
By understanding the importance and risks associated with BOMB.EXE, users can take necessary precautions and ensure the smooth operation of their systems.
Can’t Delete BOMB.EXE: Reasons and Remedies
- Step 1: Disable any running processes associated with BOMB.EXE.
- Step 2: Open Task Manager by pressing Ctrl+Shift+Esc.
- Step 3: In the Processes tab, locate and select the process related to BOMB.EXE.
- Step 4: Click on the End Task button to terminate the process.
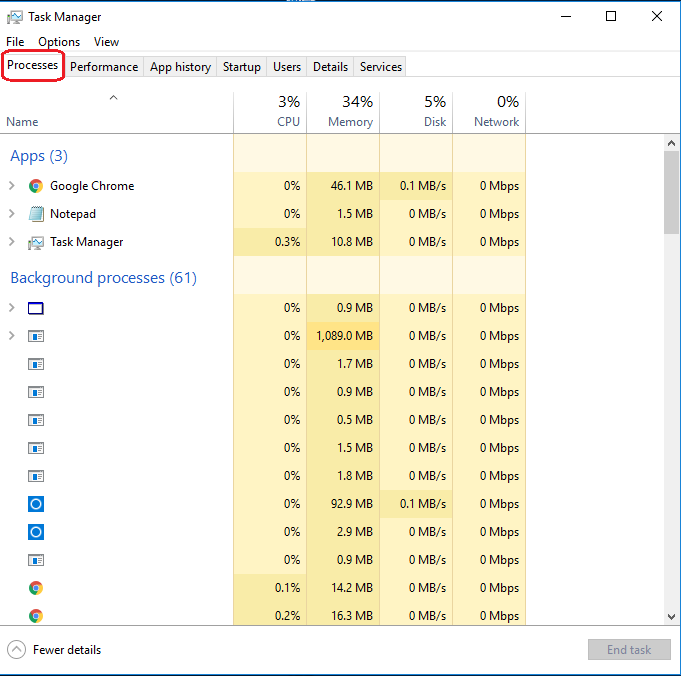
- Step 5: Close Task Manager.
- Step 6: Attempt to delete BOMB.EXE again.
- Step 7: If the file still cannot be deleted, restart your computer.
- Step 8: After the restart, try deleting BOMB.EXE once more.
- Step 9: If the file remains undeletable, boot your computer into Safe Mode.
- Step 10: To enter Safe Mode, restart your computer and repeatedly press the F8 key.
- Step 11: In Safe Mode, locate the BOMB.EXE file and attempt to delete it.
- Step 12: If all else fails, use a specialized malware removal tool to eliminate BOMB.EXE.
- Step 13: Download and install a reputable anti-malware software.
- Step 14: Run a full system scan to detect and remove any traces of BOMB.EXE.

Evaluating the Legitimacy of BOMB.EXE
When evaluating the legitimacy of BOMB. EXE, it is important to look for any reverse engineering errors and possible fixes. To begin, check for any suspicious behavior or anomalies in the binary code. Use Reverse Engineering tools like IDA Pro or Radare2 to analyze the code and identify any potential vulnerabilities or weaknesses. Additionally, conduct web searches to see if there are any writeups or forums discussing the BOMB.
EXE file. It may also be helpful to reach out to contacts in the industry or consult with vendors who specialize in reverse engineering. Finally, run the file in a secure sandbox environment to see if it exhibits any malicious behavior. By thoroughly assessing BOMB. EXE, you can determine its legitimacy and take appropriate actions to mitigate any potential risks.
BOMB.EXE Not Responding: How to Handle
When encountering a “BOMB.EXE Not Responding” error, it’s important to handle it properly to avoid any further issues. Here are some steps to help you troubleshoot and fix this problem:
1. Close the program: Start by closing the BOMB.EXE program that is not responding. Use the task manager or force quit if necessary.
2. Check system requirements: Ensure that your computer meets the minimum requirements for running BOMB.EXE. This includes the operating system, available memory, and processor speed.
3. Update BOMB.EXE: Check for any available updates for BOMB.EXE. Developers often release patches or updates to fix bugs and improve stability.
4. Scan for malware: Perform a thorough scan of your system for any malware or viruses that may be interfering with BOMB.EXE. Use reputable antivirus software for this task.
5. Check system resources: Make sure your computer has enough resources, such as available disk space and memory, to run BOMB.EXE smoothly.
6. Reinstall BOMB.EXE: If the issue persists, try uninstalling and reinstalling BOMB.EXE. This can help resolve any corrupted files or configuration issues.
Effective BOMB.EXE Removal Tools
- Use reputable antivirus software to scan for and remove BOMB.EXE
- Manually delete BOMB.EXE files and related components:
- Open File Explorer by pressing Win+E
- Navigate to the folder containing BOMB.EXE
- Select all BOMB.EXE files and press Delete
- Empty the Recycle Bin to permanently delete the files
- Terminate BOMB.EXE processes:
- Open Task Manager by pressing Ctrl+Shift+Esc
- Go to the Processes tab
- Locate any BOMB.EXE processes
- Select each BOMB.EXE process and click on End Task
- Remove BOMB.EXE registry entries:
- Open the Registry Editor by pressing Win+R, typing regedit, and pressing Enter
- Navigate to the following registry keys:
- HKEY_CURRENT_USERSoftwareBOMB.EXE
- HKEY_LOCAL_MACHINESoftwareBOMB.EXE
- HKEY_LOCAL_MACHINESoftwareMicrosoftWindowsCurrentVersionRun
- Delete any BOMB.EXE related entries by right-clicking on them and selecting Delete
- Reset web browsers to remove BOMB.EXE extensions:
- Open the affected browser
- Access the browser’s settings or options
- Locate the extensions or add-ons section
- Remove any suspicious or unwanted extensions related to BOMB.EXE
Managing BOMB.EXE at Startup
When managing BOMB.EXE at startup, it’s important to address any reverse engineering errors and find effective fixes. To begin, make sure to disable BOMB.EXE from automatically running at startup. This can be done by accessing the Task Manager and disabling the relevant startup program.
Next, it’s crucial to conduct a thorough analysis of BOMB.EXE to understand its behavior and potential vulnerabilities. This can involve reverse engineering the binary and conducting a writeup to document the findings.
If BOMB.EXE is causing issues on a webserver or cloud service, consider isolating it to prevent any potential harm to other parts of the system.
Additionally, it’s recommended to search for any available patches or updates for BOMB.EXE. The software’s official website or relevant forums can provide valuable information on fixes and improvements.
Performance Impact of BOMB.EXE on your System
The BOMB.EXE program can have a significant impact on the performance of your system. To reverse engineer any errors and find fixes, follow these steps:
1. Start by analyzing the BOMB.EXE binary using tools like IDA Pro or Radare2.
2. Look for any suspicious code or functions that could be causing performance issues.
3. Check if the program is making excessive system calls or using up too much CPU or memory resources.
4. Use static analysis techniques to understand the program’s behavior and identify any potential bottlenecks.
5. Try running the program in a controlled environment to see if it performs differently.
6. Look for any known vulnerabilities or exploits associated with BOMB.EXE.
7. Consider using dynamic analysis techniques to monitor the program’s runtime behavior and identify any performance issues.
8. Test the program on different operating systems and architectures to see if the performance varies.
9. If possible, consult the BOMB.EXE writeup or articles from folks who have encountered similar issues.
10. Finally, apply any necessary fixes or optimizations to improve the performance of the BOMB.EXE program.
Updating BOMB.EXE: Importance and Process
When it comes to updating BOMB.EXE, it is important to understand the process and its significance. Keeping your BOMB.EXE up to date ensures optimal performance and security. To update BOMB.EXE, follow these steps:
1. Start by searching for the latest version of BOMB.EXE on reliable sources such as the official website or trusted software repositories.
2. Download the updated version of BOMB.EXE and save it to your computer.
3. Before installing the new version, make sure to back up any important files or data related to BOMB.EXE.
4. Install the updated version of BOMB.EXE by running the installer or following the provided instructions.
5. After installation, launch BOMB.EXE to ensure that it is working properly and all functionalities are intact.
6. If you encounter any issues or errors during the update process, refer to the troubleshooting section in the article for possible fixes.
7. Remember to periodically check for updates to keep your BOMB.EXE software current and secure.
Downloading BOMB.EXE: Risks and Precautions
When downloading BOMB.EXE, it’s important to be aware of the risks involved and take appropriate precautions. To avoid potential harm to your computer and personal data, follow these guidelines:
1. Do not download BOMB.EXE from unknown or suspicious sources. Stick to reputable websites and platforms to minimize the risk of downloading malicious software.
2. Always use reliable antivirus software. Make sure your antivirus program is up to date and perform regular scans to detect and remove any potential threats.
3. Consider using a sandbox or virtual machine. Running BOMB.EXE in a controlled environment can help isolate it from your main operating system, reducing the risk of damage.
4. Keep your operating system and software updated. Regularly installing updates and patches can address vulnerabilities that could be exploited by malware like BOMB.EXE.
5. Exercise caution when opening email attachments or clicking on suspicious links. BOMB.EXE may be distributed through phishing emails or deceptive websites, so always be vigilant.
Windows Version Compatibility for BOMB.EXE
To ensure smooth functioning of BOMB.EXE on Windows, it is essential to consider version compatibility. BOMB.EXE is compatible with Windows 10, 8.1, and 7. For Windows 10, it is advisable to run BOMB.EXE on the latest updates to avoid any compatibility issues.
Before running BOMB.EXE, make sure to check your Windows version by:
1. Pressing the Windows key + R to open the Run dialog box.
2. Typing “winver” and pressing Enter.
3. The About Windows window will provide the version details.
If you encounter any errors while running BOMB.EXE, ensure that you have the correct Windows version and all necessary updates installed. It is also recommended to consult the BOMB.EXE Reverse Engineering Errors and Fixes article series for additional troubleshooting steps and solutions.
Safe End Task of BOMB.EXE: What You Should Know
When dealing with BOMB.EXE, it’s crucial to know how to safely end the task without causing any harm. Here are some important tips to keep in mind:
1. Terminate the process: Use the Task Manager or a similar tool to end the BOMB.EXE process. This will stop the execution of the binary and prevent any further damage.
2. Avoid manual deletion: Do not attempt to delete the BOMB.EXE file manually as it may have associated dependencies. Use a trusted antivirus or anti-malware software to handle the removal.
3. Scan for malware: After terminating the process, perform a thorough scan of your system using reputable antivirus software. This will help identify any remaining traces of the BOMB.EXE and ensure your system is clean.
4. Consider cloud-based solutions: If you suspect BOMB.EXE is connected to a cloud service or hosting platform, reach out to the relevant service provider for assistance. They may have specific steps or tools to help address the issue.
Exploring Alternatives to BOMB.EXE
If you’re looking for alternatives to BOMB. EXE for reverse engineering errors and fixes, there are a few options to consider. One alternative is to use IDA Pro, a powerful and widely used disassembler and debugger. It offers advanced features for analyzing binary files and can help identify and fix errors in the code.
Another option is Ghidra, an open-source reverse engineering tool developed by the National Security Agency. It provides a comprehensive set of features for analyzing and reverse engineering binary files. Additionally, Radare2 is another popular choice that is free and open-source. It supports various architectures and offers a range of functionalities for analyzing and debugging binaries.
These alternatives can be valuable tools for reverse engineering errors and fixing them effectively.
